Internet Facing Applications
Protect Your Most Exposed Applications
Prevent exploits and malicious code from ever running inside the application.
Book a demo
Internet-Facing Applications Are the First to Break

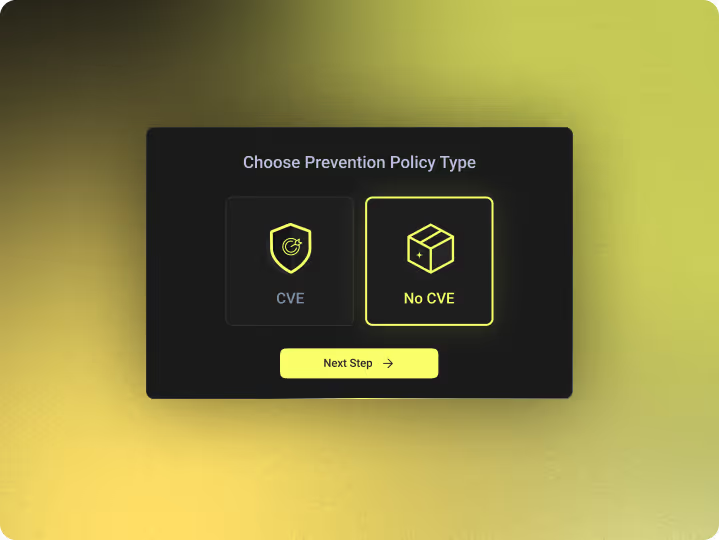
Zero-Day & No-CVE Attacks
Traditional tools depend on known signatures or CVEs. 70% of real-world attacks don’t have a CVE.

The Exposure Window
Even when a vulnerability is known, patching takes time. Attackers move much faster than fixes.

WAF is Not Enough
WAFs can’t see what actually executes inside the application once traffic is allowed.
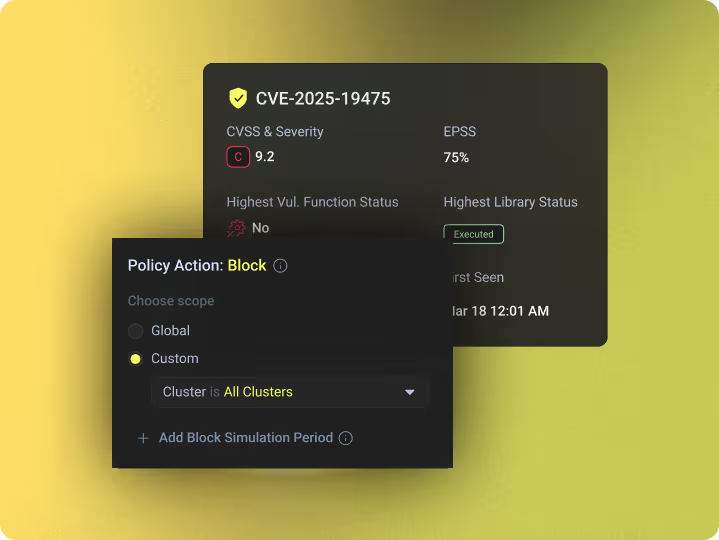
True Runtime Prevention
Raven stops malicious code inside the application, at execution time.
- Prevents malicious code before it runs
- Works with or without a known CVE
No Exposure Window
Stay protected immediately, even while fixes are pending.
- No code changes required
- No emergency patch cycles
- Protection applies instantly in production.
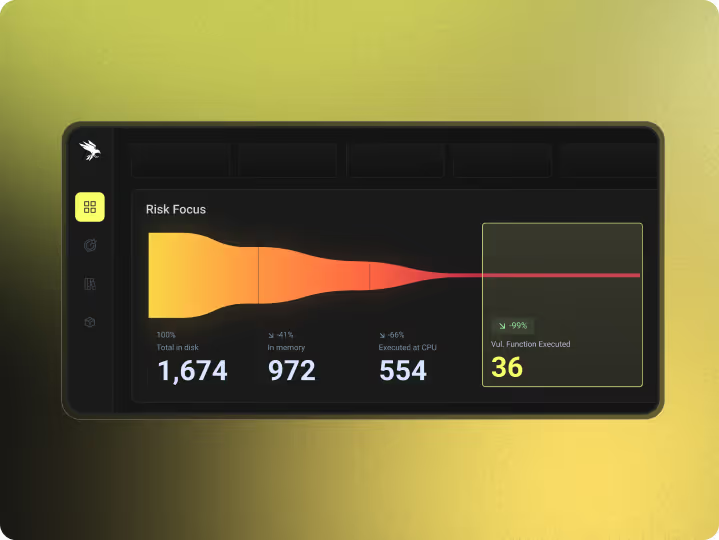
Runtime-Aware Risk Reduction
Raven stops malicious code inside the application, at execution time.
- Prevents malicious code before it runs
- Works with or without a known CVE
1 in 8 Billion
1 false positive in 8 billion events
<0.2% CPU
Best in class performance
Protect Your Most Exposed Applications
Book a demo%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more

.svg)