Database Protection
Stop SQL Injection Inside the Application
Prevent SQL injection at execution time - before malicious queries ever reach the database.
Book a demo
SQL Injection In the AI Era

Obfuscation Wins
Attackers evade signature-based tools with AI encoding & obfuscation

WAF Blindness
WAFs can’t see what executes once traffic is allowed

AI Makes It Worse
AI generates infinite SQLi variants that bypass rules instantly
In-Application SQL Injection Prevention
Raven prevents SQL injection from inside the application, by monitoring the SQL client libraries that actually generate and execute database queries.
No network traffic inspection. No signatures or rules.
Raven observes how queries are constructed and executed in real time, and blocks malicious execution at the source.
No network traffic inspection. No signatures or rules.
Raven observes how queries are constructed and executed in real time, and blocks malicious execution at the source.
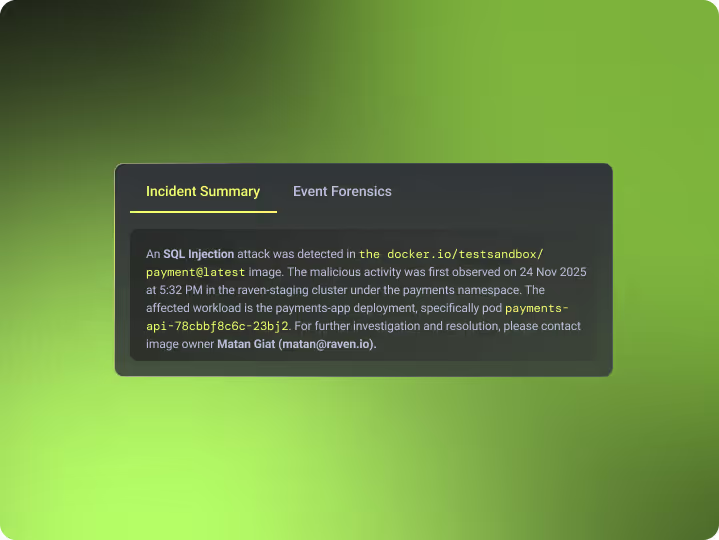

Obfuscation-Proof by Design
Raven operates after the query is constructed, at execution time inside the application - not at the network edge. This makes Raven immune to query obfuscation, encoding tricks, parameter smuggling and AI-generated payloads.
If the execution is malicious, it’s blocked.
If the execution is malicious, it’s blocked.
Zero Rules. Zero Maintenance.
Traditional SQL injection defenses require constant rule updates, new signatures and emergency tuning after bypasses.
Raven requires none of that.No rules to write.
No signatures to maintain. No tuning for new attack techniques.
Protection adapts automatically because it’s based on runtime execution behavior, not static detection logic.
Raven requires none of that.No rules to write.
No signatures to maintain. No tuning for new attack techniques.
Protection adapts automatically because it’s based on runtime execution behavior, not static detection logic.
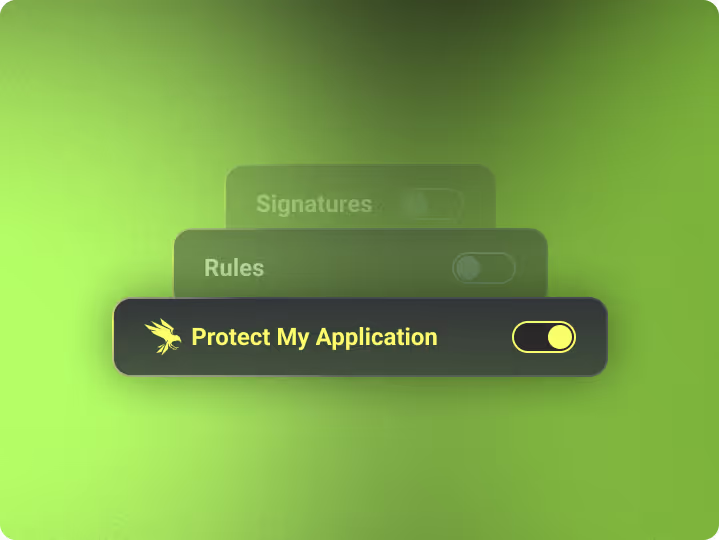
Rule-less Detection
No signatures. No allowlists. No maintenance.
Execution-Level Accuracy
Detects SQL injection other tools cannot see.
<0.2% CPU Overhead
Safe to run in high-throughput production systems.
See SQL Injection Blocked at Execution Time
Book a demo%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more

.svg)