High-Compliance Environments
Runtime enforcement for regulated industries
Security controls must be enforced - not just documented. Documentation alone does not reduce runtime risk in regulated environments.
Book a demo
Most security tools only observe.

Controls are advisory, not enforced
Most tools generate alerts and reports, but allow risky code paths to execute in production - even in regulated environments.

Evidence is indirect and noisy
Audits rely on scan results, CVE counts, and policies that don’t reflect what actually ran in production.

Runtime risk changes faster than compliance cycles
CI/CD velocity, dependency churn, and AI-generated code invalidate static controls within days.
Enforced Runtime Controls (Not Just Detection)
With Raven, compliance teams gain real enforcement, not best-effort monitoring. Raven doesn’t rely on alerts or dashboards alone, it actively prevents malicious execution paths in production - including known CVEs, CVE-Less and abused legitimate libraries.
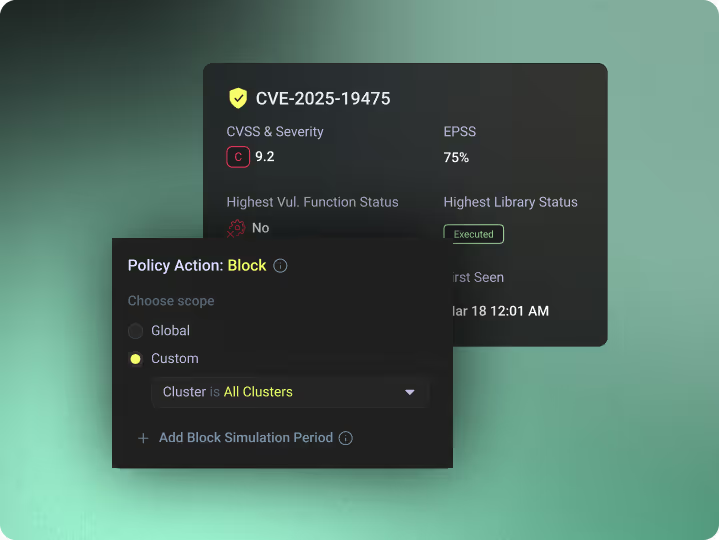
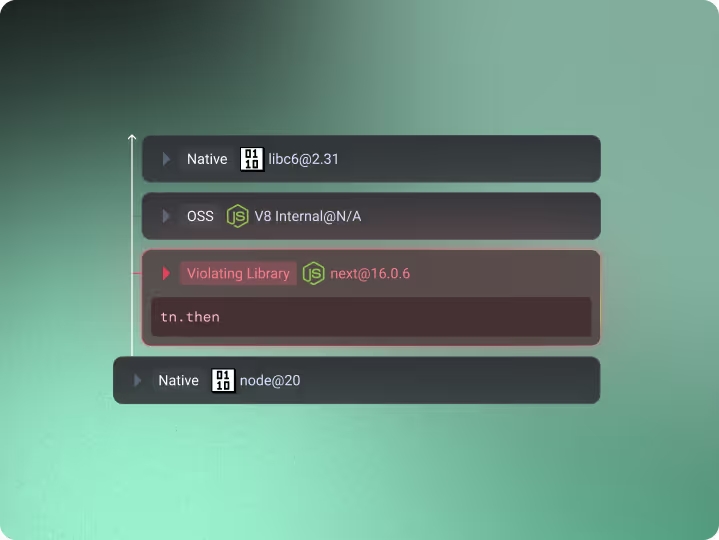
Audit-Ready Runtime Evidence
Raven records what actually executed in production like which libraries ran, which functions were invoked, and which execution paths were blocked or allowed.With Raven, Audits are based on runtime truth, not theoretical exposure.
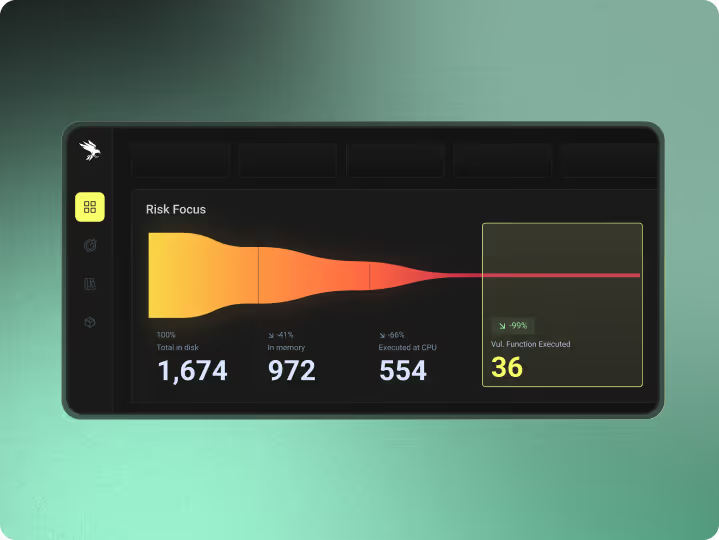
Reduced Vulnerability Noise
While traditional SCA overwhelms regulated teams with thousands of findings, Raven demonstrates risk-based prioritization, aligned with compliance intent.
Raven Runtime SCA:
- Focuses only on executed code paths
- Deprioritizes vulnerabilities that never run
- Aligns remediation with real production risk
.avif)
Where this is used
Common regulated environments
- Fed-Ramp Environments
- Financial services & FinTech
- Healthcare & life sciences
- Enterprise SaaS with SOC 2 / ISO 27001 obligations
- Platforms with customer-facing SLAs
- Organizations with strict change-control requirements
- PCI DSS 4
Enforce Security at Runtime
Book a demo%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more

.svg)