Runtime ADR
Protect the application from within
Raven ADR, runs inside the application, detects real application attacks as they execute, with deep, library and function-level forensics that traditional tools never see.



Attacks hide inside application logic
Modern attacks don’t look like malware.They abuse legitimate libraries, frameworks, and execution paths, blending into normal application behavior. Infrastructure and network-level tools miss this entirely.
Traditional detection lacks application context
EDR, CWPP, and SIEM tools see processes, files, and network events - not why code executes or how execution flows through the application. Without application context, alerts are noisy and response is slow.
Language Sprawl
Companies run applications across an average of nine programming languages. Real protection requires a security solution that supports them all.
Features
Application. Detection. Response
True application-level visibility
Raven sees real execution inside the application - down to libraries, functions, and call paths. This visibility is what makes accurate detection and fast response possible, without guessing or heuristics.
Library level forensics
Built on eBPF and Raven’s patented Library level monitoring technology, every execution is captured as a deterministic call flow: which libraries ran, in what order, and how execution deviated during an attack.

.png)
Developer Attribution & Code Provenance
Raven traces runtime attacks back to the exact code change that introduced the risk.Each exploit is mapped to the owning commit, author, deployment, and service — turning incidents into actionable developer context, not generic alerts.
Security sees what happened.
Developers see where it came from and how to fix it.
Security sees what happened.
Developers see where it came from and how to fix it.
.png)

Runtime Drift
Raven detects changes in application behavior at runtime - not just configuration drift, but execution drift. Raven identifies unexpected package installs, unauthorized binaries, and new code paths, exposing supply-chain abuse, post-exploit persistence, and living-off-the-land attacks in real time.

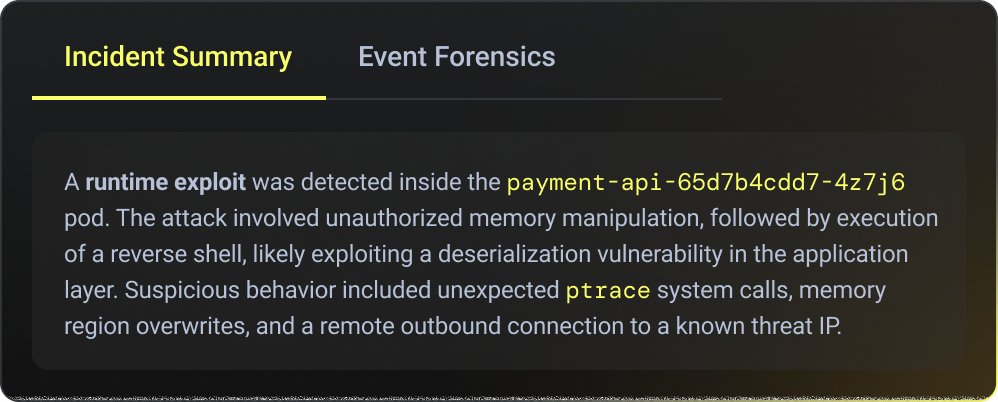
SQLi Abuse Detection
Raven detects SQL injection and database abuse from inside the application runtime, not from network patterns or query signatures. This is done by observing real execution paths, input flow, and query construction. This enables high-fidelity SQLi detection with full application context, even for dynamic or obfuscated queries, without regexes, payload guessing, or WAF false positives.

.png)








.png)



Frequently Asked Questions
What program languages does Raven support?
.svg)
Raven is Language-agnostic by design. Raven works across modern across all major languages. without language-specific agents or rules. One model. One view. No blind spots. The program languages supported by Raven: Java (and any JVM based programming language), JavaScript (Node.js), Python, Go, Ruby, C++, C, Rust, PHP, Scala, Kotlin.
Is Raven built for production?
.svg)
Yes! Raven is built for production. Raven is designed to run continuously in high-throughput, real-world production environments. No code injection. No request replay. No data exfiltration pipelines that break at scale.
What is Runtime ADR?
.svg)
Runtime ADR (Application Detection & Response) is a security approach that detects and responds to attacks from inside the running application, based on real code execution - not network traffic, signatures, or known malware patterns.
How is Runtime ADR different from EDR, CWPP, or WAF?
.svg)
EDR, CWPP, and WAF operate outside the application, focusing on processes, files, network requests, or known patterns.
Raven ADR runs inside the application runtime, understanding which libraries and functions executed and how execution flows changed during an attack.
Raven ADR runs inside the application runtime, understanding which libraries and functions executed and how execution flows changed during an attack.
Does Raven ADR rely on CVEs or signatures?
.svg)
No. Raven ADR does not rely on CVEs, signatures, or predefined attack rules.
It detects abnormal execution behavior at runtime, allowing it to identify attacks even when no CVE exists.
It detects abnormal execution behavior at runtime, allowing it to identify attacks even when no CVE exists.
How does Raven reduce false positives?
.svg)
Raven observes actual execution paths - which libraries ran, in what order, and how execution deviated.
This context eliminates guesswork and heuristics, resulting in high-fidelity alerts with statistically negligible false positives.
This context eliminates guesswork and heuristics, resulting in high-fidelity alerts with statistically negligible false positives.
Can Raven ADR help developers remediate issues?
.svg)
Yes. Raven automatically maps runtime attacks back to the exact code change, including the commit, author, deployment, and service.
Security teams understand what happened - developers see where it came from and how to fix it.
Security teams understand what happened - developers see where it came from and how to fix it.
How is Raven ADR deployed?
.svg)
Raven ADR is deployed as a lightweight runtime component and integrates via standard deployment workflows (e.g., Kubernetes, Helm).
It requires no code changes, no code injection, and no request replay, and can be enabled incrementally per service or environment.
It requires no code changes, no code injection, and no request replay, and can be enabled incrementally per service or environment.
What is the performance impact?
.svg)
Best in class Performance: <0.2% CPU &<300MB RAM, when all modules are active. Raven is designed for high-throughput production environments. It analyzes execution at the library and function level using eBPF-based instrumentation, with negligible runtime overhead and no impact on application latency or stability.
Resources
%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more
.svg)

