Application-Aware Cloud Threat Hunting
Application-Aware Cloud Threat Hunting
Hunt threats using real application execution - not just infrastructure signals
Book a demo
SOCs hunt threats without application visibility

Infrastructure signals lack application context
Cloud logs, network telemetry, and CSP alerts show where something happened - not what code executed or why.

Alert fatigue without application relevance
SOCs are flooded with detections that can’t be tied to real application behavior, leading to false positives and slow investigations.

AppSec and SOC operate with different truths
AppSec sees vulnerabilities.SOC sees incidents.Neither can answer: Why did the code execute? Is it a feature or an actual attack?
Application-Aware Threat Signals
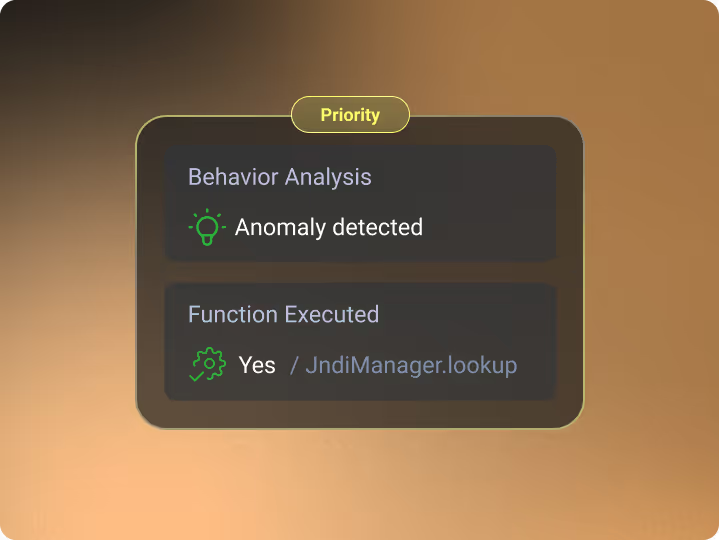
With Raven, SOC analysts gain deterministic context instead of probabilistic alerts.
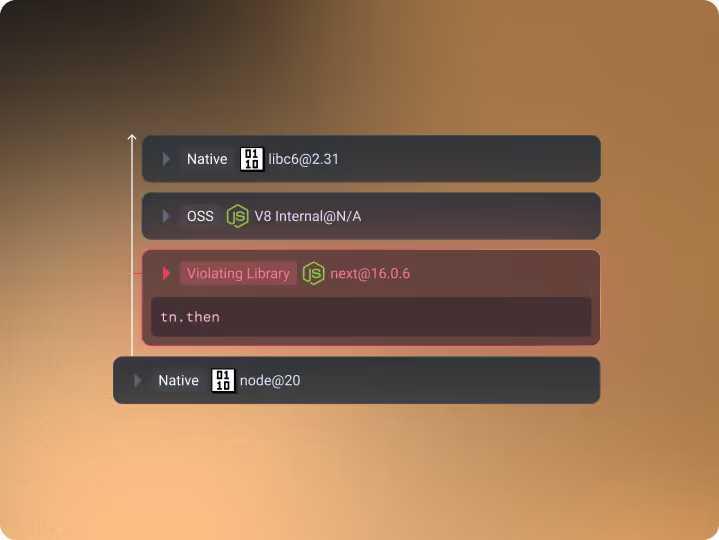
Raven surfaces high-fidelity signals such as:
- Which libraries were invoked
- Which functions executed
- Whether execution matched expected behavior
- Whether execution was blocked or allowed
Faster, More Accurate Investigations
With Raven, Mean Time To Investigate (MTTI) drops dramatically.
During an investigation, Raven answers:
- Did this alert involve real code execution?
- Was the behavior legitimate or abused?
- Was a vulnerable function actually invoked?
Bridge Between SOC and AppSec
With Raven, SOC and AppSec operate from a shared runtime truth.
Raven connects:
- Runtime SCA (what is vulnerable)
- ADR (what is malicious)
- Execution context (what actually happened)

Amplify your SOC with application context
Book a demo%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more

.svg)