Runtime SCA
If it doesn’t run,
it doesn’t matter.
Runtime SCA that cuts through the noise and shows what truly is exploitable.



CVSS scores are static and Generic
CVSS scores ignore how your application actually runs, which functions execute, and whether a vulnerability is even reachable in production.
Drowning in Vulnerabilities
Modern applications ship thousands of CVEs. Most are never executed, yet teams are forced to triage everything - wasting time on risk that doesn’t exist.
Static scanners fall short
Static Scans Can’t See Runtime Reality, they detect code on disk, not code in motion. They miss dynamic loading, feature flags, real execution paths, and what attackers can actually reach.
Features
Your vulnerability backlog doesn’t stand a chance
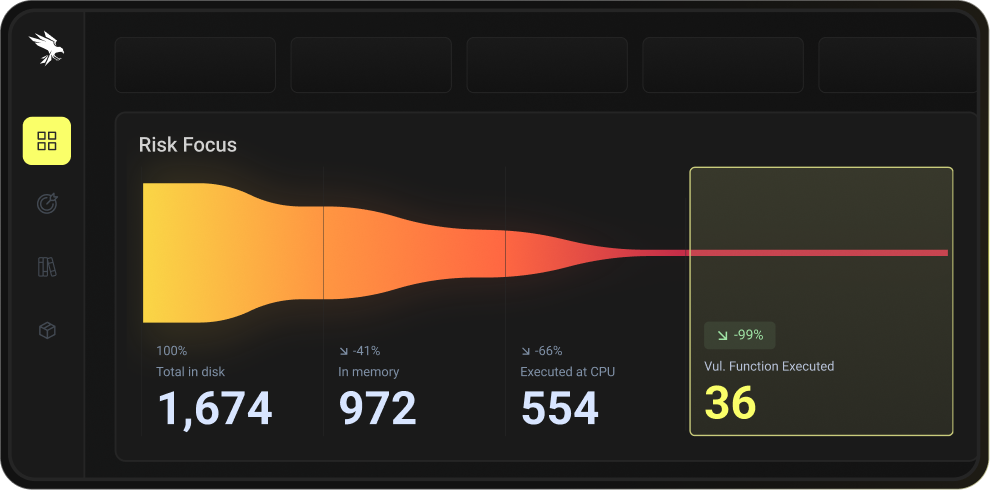
Runtime Deprioritization
De-prioritize 97%-99% of vulnerabilities with function-level runtime reachability. Determine which vulnerabilities pose the highest risk, and remediate those first.

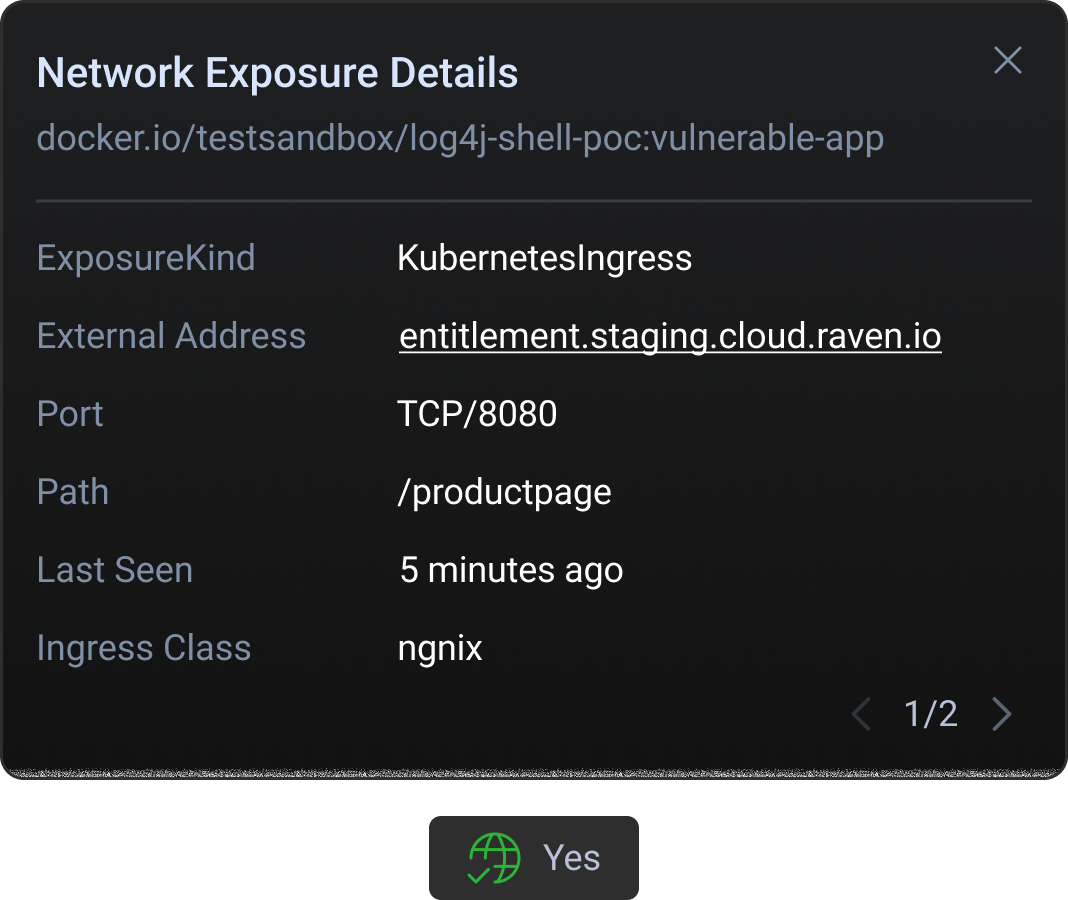
Runtime Network reachability
Find out which workloads are facing the internet and prioritize remediation for those first. By collecting cluster metadata we are able to piece together your container network exposure path and prioritize your vulnerabilities accordingly.

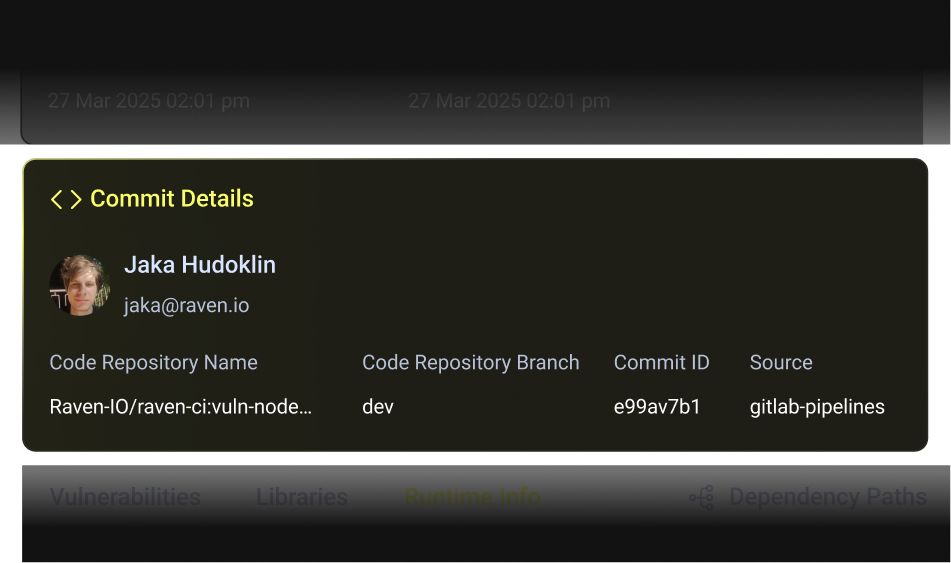
Full Code-to-Runtime Visibility
Raven traces runtime behavior all the way back to its origin in code.Every executed library, function, and exploit path is mapped to the exact commit, author, build, image, and deployment that introduced it. Security teams see what happened in production. Developers see where it came from and how it shipped.
No guesswork. No log correlation. No manual forensics.
No guesswork. No log correlation. No manual forensics.

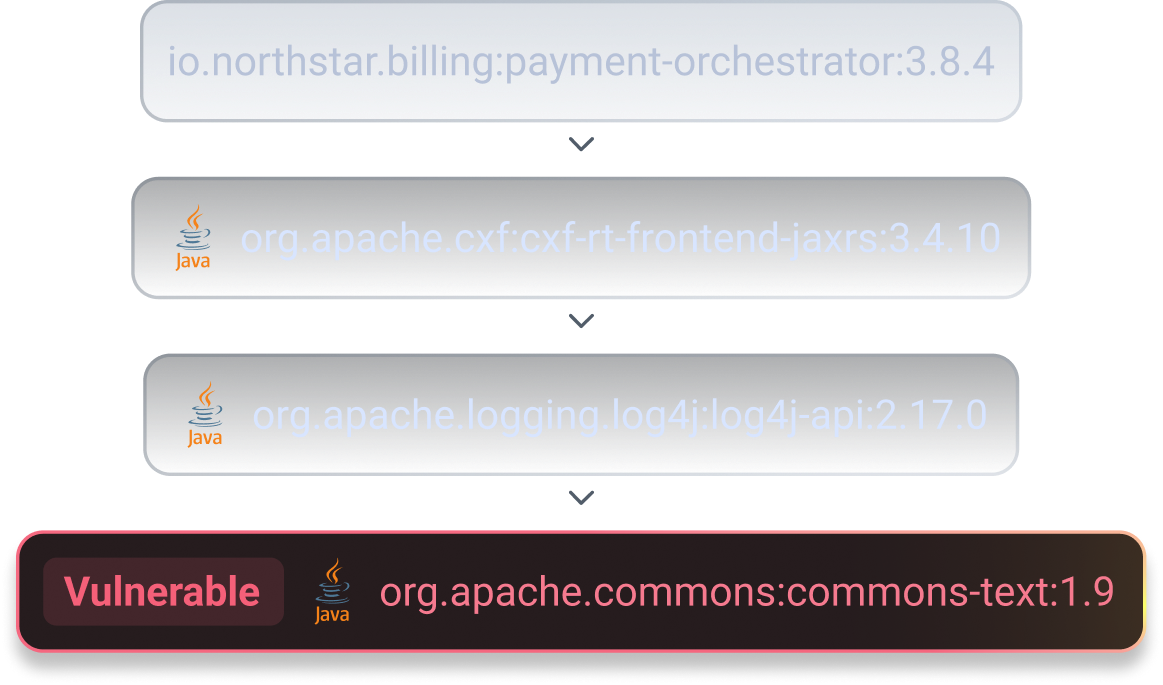
Full remediation path visualization
Raven accelerates remediation by visualizing full dependency paths, exposing hidden risks in deep transitive dependencies. By untangling complex dependency trees, it makes vulnerabilities easy to identify, understand, and fix across your entire stack.
Integrations
Streamline security workflows through seamless integrations with messaging and issue-tracking tools. Automatically push customized security feeds and vulnerability discoveries directly into Slack, Teams or email for enhanced team communication. Create targeted JIRA tickets based on configurable security rules, ensuring alerts always reach the right teams for efficient remediation and improved collaboration.








.png)



Frequently Asked Questions
How is Runtime SCA different from traditional SCA tools?
.svg)
Traditional SCA reports every known vulnerability in your dependency tree. Raven focuses only on vulnerabilities that actually execute and can be exploited in production, reducing noise by up to 99%.
Does this require source code access?
.svg)
No. Raven reconstructs dependency relationships and vulnerable execution paths from runtime behavior, without needing source code or build pipelines.
How accurate is the runtime reachability analysis?
.svg)
Raven observes real execution at the function level. If a vulnerable function never executes, it’s deprioritized. If it does, Raven surfaces it with full context.
Does Runtime SCA impact performance?
.svg)
Best in class Performance: <0.2% CPU & <300MB RAM, when all modules are active. Raven is designed for high-throughput production environments. It analyzes execution at the library and function level using eBPF-based instrumentation, with negligible runtime overhead and no impact on application latency or stability.
Resources
%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more
.svg)

