Runtime Prevention
Stop malicious code from being executed. CVE or No CVE.
Prevent exploits and malicious code from ever running inside the application.



Attacks move faster than fixes
Vulnerabilities are often exploited within hours or days of public disclosure. With AI-assisted exploit generation, attackers now weaponize flaws before patches, signatures, or rules can exist.
70% of exploits have no CVE at all
In order to keep up with sophisticated attackers and ensure the security of modern cloud applications, organizations must detect attacks without relying on existing CVE signatures.
WAF is not enough
WAFs operate outside the application and rely on known patterns, signatures, and request inspection. Modern attacks execute inside application logic, often after the request is already allowed.Once execution moves in-process, WAFs are blind.
Features
Stop Exploits with One Click.
Raven prevents abnormal execution at runtime before malicious code executes.No signatures. No WAF rules. No reactive patch cycles.
Stop CVE Exploits
When a known CVE is exploited, Raven prevents the exploit at the exact moment it occurs.
.png)

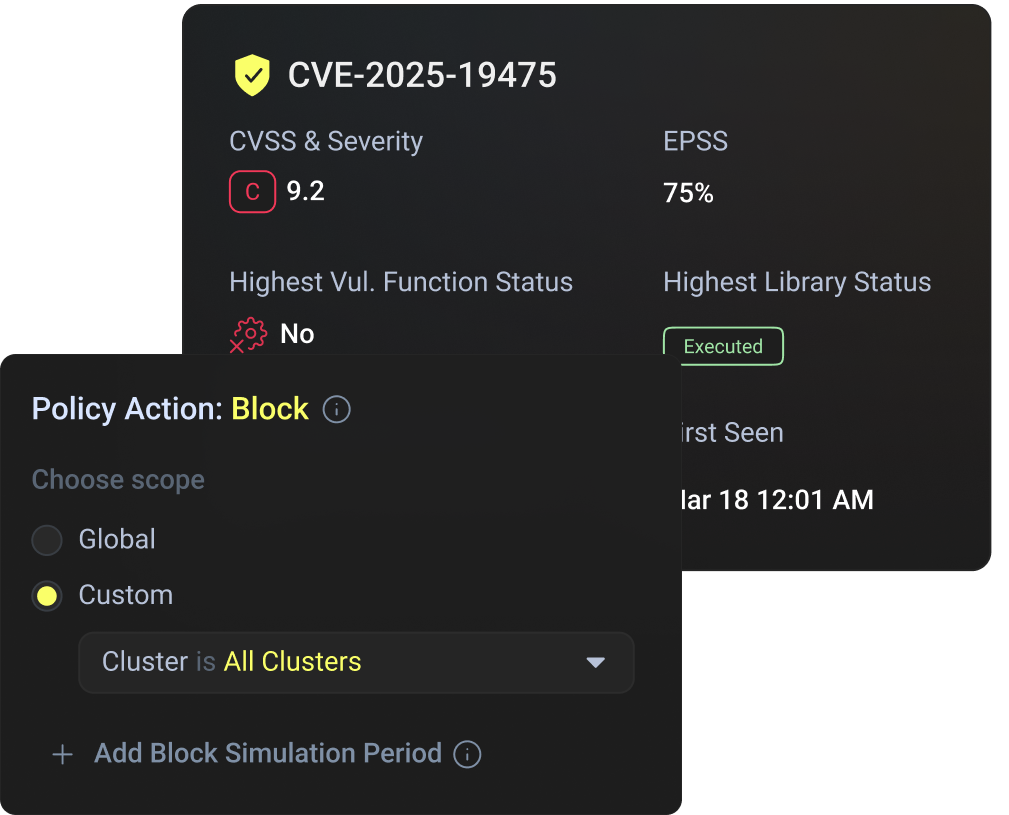
Stop CVE-less Exploits
Even with No CVE present, the attack changes the application’s execution flow. Raven detects that abnormal execution at runtime and prevents the exploit at the exact moment it occurs.









.png)



Frequently Asked Questions
What is Runtime Prevention?
.svg)
Runtime Prevention is a security approach that stops malicious code at the moment it attempts to execute inside the application. Instead of detecting attacks after impact or relying on signatures, Runtime Prevention blocks abnormal execution in real time.
How does Runtime Prevention stop malicious code execution?
.svg)
Runtime Prevention continuously observes how an application executes code. When an exploit attempts to alter normal execution flow, the system blocks the execution before malicious code runs, preventing damage at the source.
Does Runtime Prevention require a known CVE?
.svg)
No. Runtime Prevention works with or without a CVE. It stops known vulnerabilities, zero-day exploits, and CVE-less attacks by detecting abnormal execution behavior, not by matching vulnerability signatures.
How is Runtime Prevention different from detection-based security?
.svg)
Detection-based tools alert after suspicious activity occurs. Runtime Prevention actively blocks malicious execution during runtime, preventing exploitation instead of reporting it after the fact.
Where is Runtime Prevention typically deployed?
.svg)
Runtime Prevention is typically deployed on internet-facing servers and applications that are exposed to real-world attacks. These environments carry the highest risk and benefit most from runtime prevention.
Is Runtime Prevention suitable for internal or non-internet-facing applications?
.svg)
Yes. While Runtime Prevention is most commonly used for internet-exposed workloads, it can also protect internal services, APIs, and backend applications where exploitation risk exists.
How is Runtime Prevention different from WAF?
.svg)
WAFs operate outside the application and rely on request patterns and signatures. Runtime Prevention operates inside the application, where actual code execution happens. Once an attack reaches in-process execution, WAFs cannot stop it - Runtime Prevention can.
Can Runtime Prevention stop zero-day exploits?
.svg)
Yes. Runtime Prevention does not rely on prior knowledge of an exploit. If an attack causes abnormal execution inside the application, it is blocked immediately, even if the vulnerability has never been disclosed.
What types of attacks can Runtime Prevention block?
.svg)
Runtime Prevention can block:Remote Code Execution (RCE)
- Injection attacks (SQL, command, template)
- Deserialization exploits
- Supply-chain attacks executed at runtime
- Abuse of legitimate libraries and frameworks
Protection is based on execution behavior, not attack patterns.
Does Runtime Prevention rely on signatures or rules?
.svg)
No. Runtime Prevention does not depend on signatures, static rules, or reactive patching. Protection is driven by real-time execution analysis.
Does Runtime Prevention require application code changes?
.svg)
No. Runtime Prevention protects applications without modifying source code, recompiling binaries, or requiring developer instrumentation.
Can Runtime Prevention break applications?
.svg)
Runtime Prevention is designed to block only malicious execution paths. Normal application behavior is not affected.
Where does Runtime Prevention run?
.svg)
Runtime Prevention operates within the application environment, monitoring execution in real time. It is suitable for cloud-native, containerized, VM-based, and traditional application deployments.
Is Runtime Prevention only for production environments?
.svg)
Runtime Prevention is typically deployed in production environments to stop live attacks, but it can also be used in staging or pre-production to validate protections before release.
Who should use Runtime Prevention?
.svg)
Runtime Prevention is used by:
- Application Security teams
- Security Engineering teams
- DevSecOps teams
protecting internet-facing applications where attacks move faster than patches.
How does Runtime Prevention complement CI/CD security?
.svg)
CI/CD security prevents risky builds from shipping. Runtime Prevention stops attacks that still reach production. Together, they provide prevention before deployment and prevention during execution.
Resources
%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more
.svg)

