Runtime AI-Agents
No AI Agent Can Hide
Discover, monitor, and control every AI agent operating in your environment.



AI agents act inside application logic
Agents don’t look like malware. They use legitimate libraries, frameworks, and APIs to reason, plan, and execute actions - blending into normal application behavior. Traditional security tools can’t distinguish intent from abuse.
Shadow AI is invisible to existing tools
Most AI agents are created by developers, teams, or vendors without centralized security approval. They bypass IAM reviews, policy enforcement, and audit trails - yet still access production data and systems.
External controls lack runtime context
Network controls, API gateways, and IAM policies see requests, not agent decisions. Once an agent operates in-process, these tools lose visibility and control.
Features
Discover. Observe. Control AI Agents.
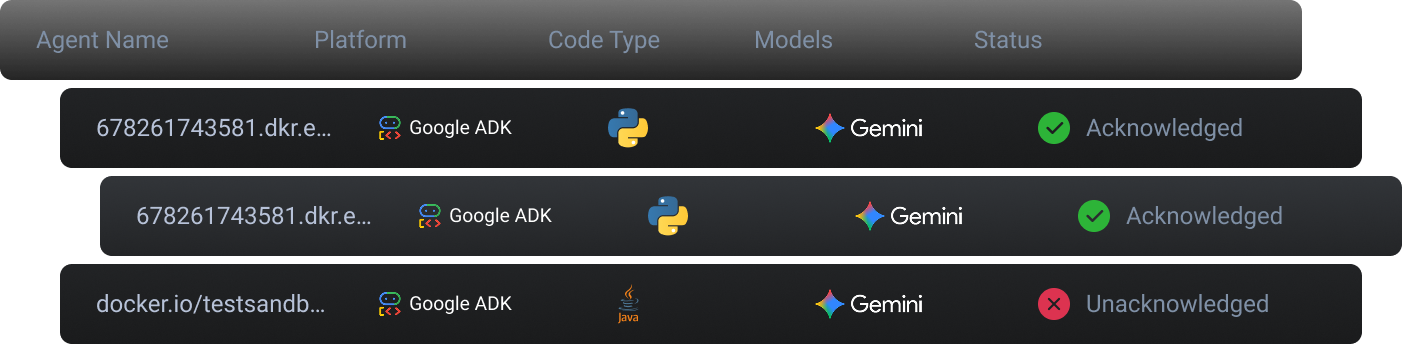
Runtime AI Agent Discovery
Raven automatically discovers AI agents running in production, including embedded agents, frameworks, and tool-driven workflows.No registration. No tagging. No manual inventory.

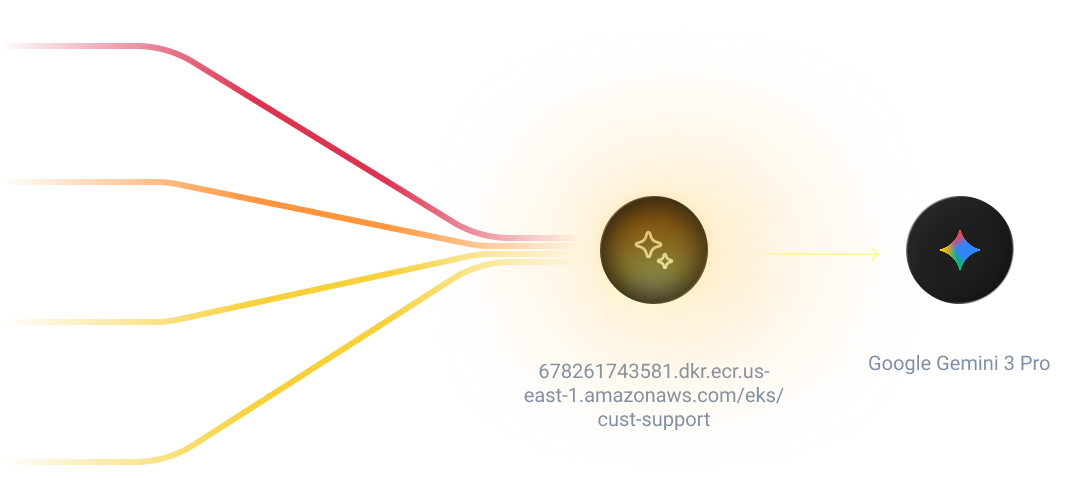
Real Behavior Monitoring
Raven monitors what agents actually do at runtime, what data they access, the APIs and tools they invoke and the code paths they execute. This exposes risky behavior that static reviews and configs never catch.
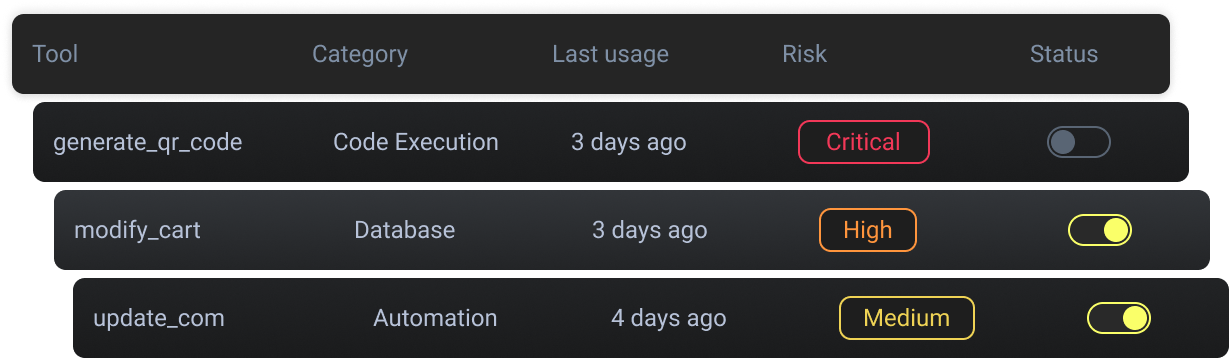
Policy-Based Runtime Control
Security teams define what agents are allowed to do - not just who they are.
Raven can alert or block unsafe actions in real time, before data leaks or misuse occurs.
Raven can alert or block unsafe actions in real time, before data leaks or misuse occurs.

Developer Attribution & Accountability
Every agent action is traced back to the owning service, deployment, code change and author.
Security gets visibility. Developers get clarity and ownership.
Security gets visibility. Developers get clarity and ownership.

.png)








.png)



Frequently Asked Questions
What is Raven Runtime AI Agents?
.svg)
Raven Runtime AI Agents provides real-time visibility and control over AI agents operating inside production applications. It discovers both approved and shadow AI agents, monitors their real behavior at runtime, and enforces security policies before unsafe actions cause damage.
How is this different from AI guardrails or prompt monitoring?
.svg)
Guardrails and prompt monitoring operate at the model or request layer. Raven operates inside the application runtime, observing what agents actually do, which data they access, which APIs they call, and which code paths they execute. This allows Raven to detect and stop abuse that external controls cannot see.
Does Raven require code changes or agent instrumentation?
.svg)
No. Raven does not inject code, modify prompts, or require language-specific SDKs. It passively observes runtime execution using low-overhead instrumentation designed for production environments.
What types of AI agents does Raven support?
.svg)
Raven supports AI agents across modern polyglot environments, including Java, Node.js, Python, Go, and more. It works with embedded agents, framework-based agents, and tool-driven workflows, without requiring agent-specific integration.
Can Raven block unsafe AI agent actions?
.svg)
Yes.
Raven can alert on or block unsafe agent behavior in real time, such as unauthorized data access, unexpected tool execution, or risky code paths, before damage occurs.
Raven can alert on or block unsafe agent behavior in real time, such as unauthorized data access, unexpected tool execution, or risky code paths, before damage occurs.
How does Raven handle performance impact?
.svg)
Raven is built for high-throughput production workloads. It uses efficient runtime instrumentation and does not replay requests, intercept prompts, or stream large volumes of data externally. Customers run Raven continuously with minimal performance overhead.
How does Raven help developers remediate AI agent risks?
.svg)
Raven traces agent actions back to the owning service, deployment, and code change. Security teams see what happened, and developers see exactly where the behavior originated and how to fix it, turning incidents into actionable feedback.
Is customer data sent outside the environment?
.svg)
No. Raven does not exfiltrate application data, prompts, or payloads for external analysis. Detection and enforcement happen at runtime, inside the environment, preserving data privacy and scalability.
Resources
%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more
.svg)

