Runtime CI/CD Gatekeeper
Stop Risky Builds Before They Ship
Bring runtime application intelligence into the release process to identify and stop dangerous builds before they reach production



CI Blocks the Wrong Things
Traditional CI security gates fail builds based on CVSS scores, unused dependencies, and theoretical risk, forcing teams to fix vulnerabilities that will never execute in production.
Security Signals Are Fragmented
Vulnerabilities, exploitability, malware, licenses, and network exposure are enforced by different tools, at different stages, with inconsistent logic and zero shared context.
Developers Don’t Trust the Gate
When CI blocks builds without clear, runtime-backed reasoning, developers bypass security, add exceptions, or disable gates entirely, turning “shift left” into noise.
Features
Runtime-Aware CI/CD
Runtime-Aware CI/CD Policies
Create build policies based on predicted runtime execution - which functions, libraries, and code paths are expected to run in production.
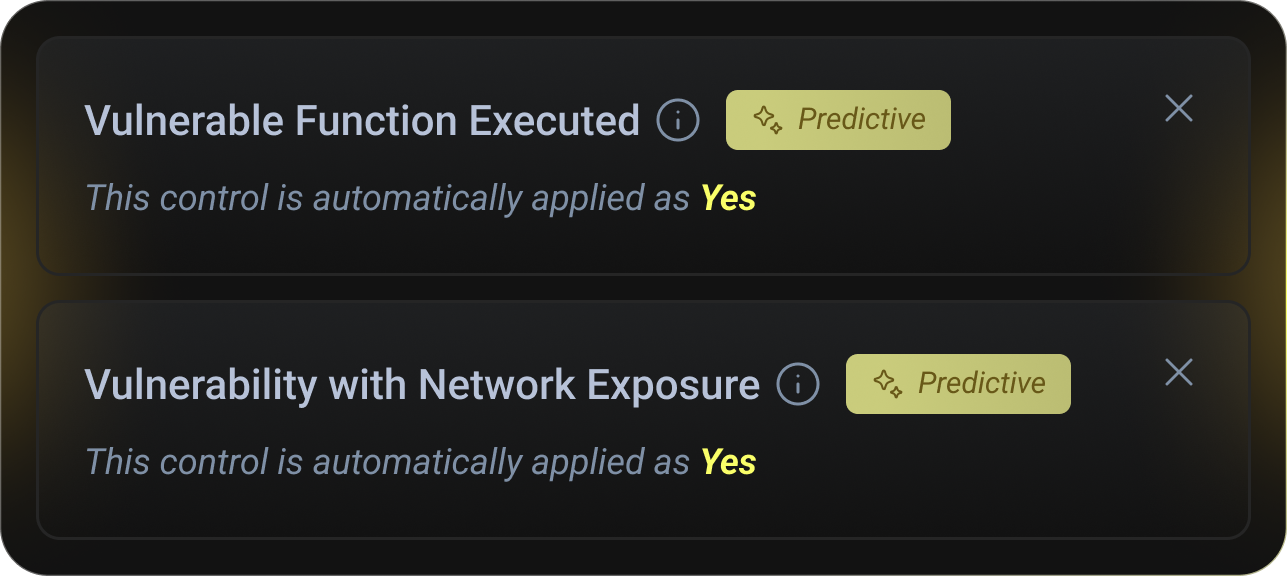


Exploit & Exposure-Based Gating
Block builds only when vulnerable code is reachable and exploitable, using network exposure, CVSS, EPSS, and known-exploited intelligence.

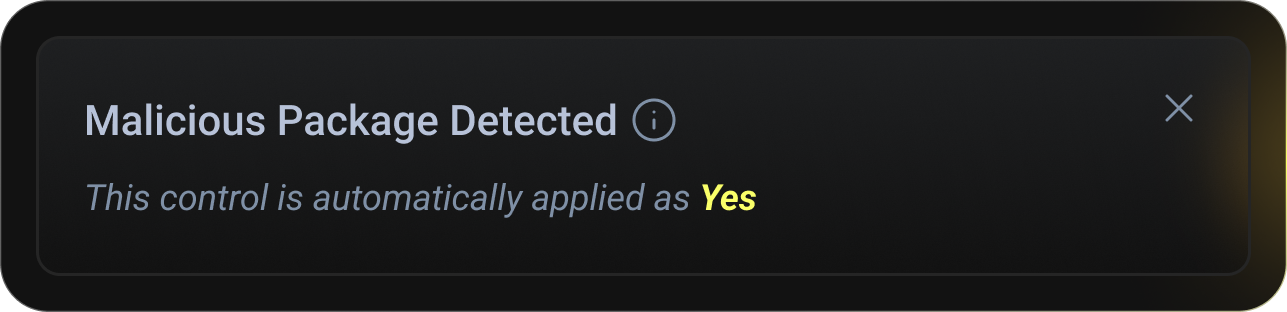
Supply Chain Risk Prevention
Stop malicious packages, compromised dependencies, and risky artifacts before they enter production.

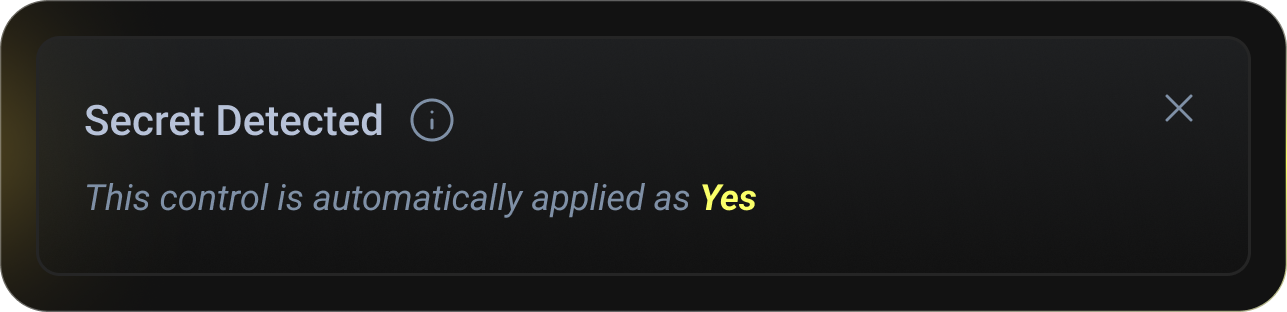
Secrets & Credential Detection
Detect leaked secrets, credentials, and sensitive tokens during build and fail the pipeline automatically.

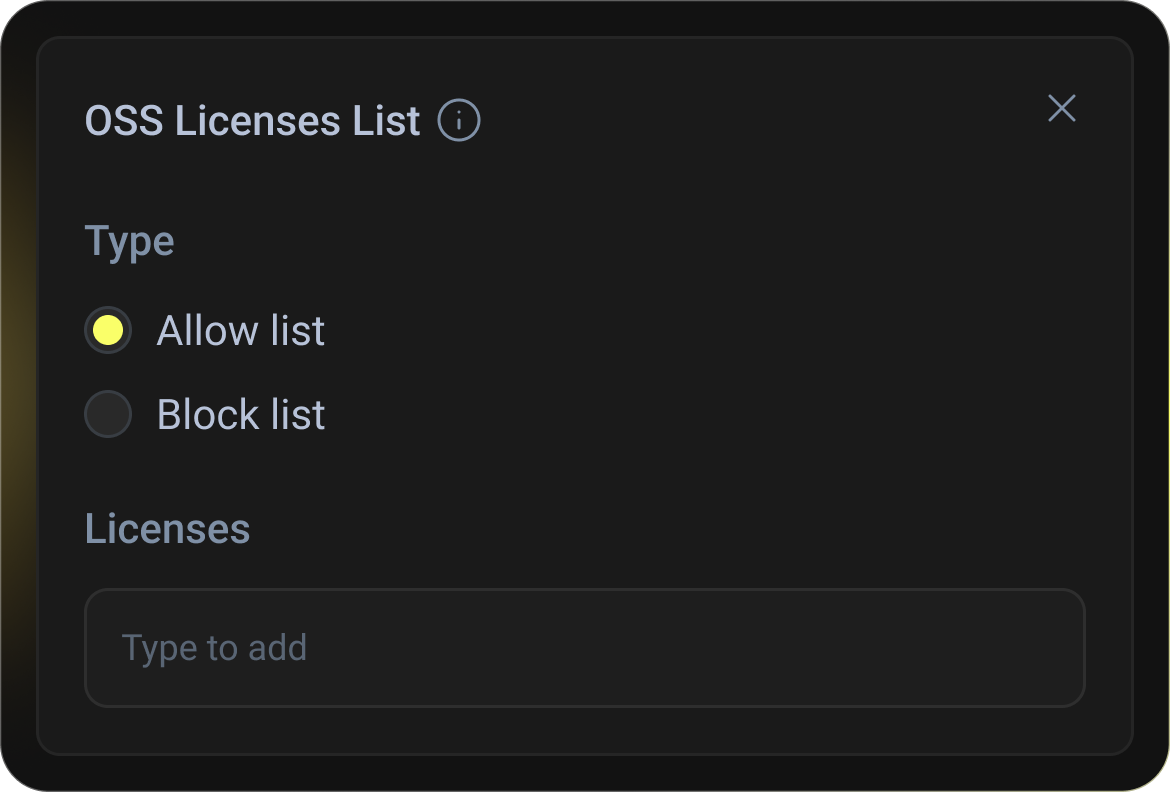
OSS License & Compliance Enforcement
Enforce granular allow/deny rules for open-source licenses directly in CI.

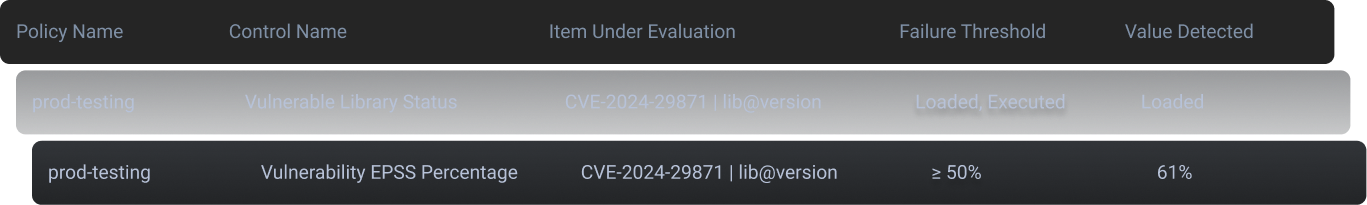
Deterministic Policy Enforcement
Each control is evaluated independently during the build. If any rule fails, the artifact is blocked - no ambiguity, no blended scores.









.png)



Frequently Asked Questions
What is a Runtime CI/CD Gatekeeper?
.svg)
A Runtime CI/CD Gatekeeper is a security control that blocks builds during CI/CD based on predicted runtime behavior, not just static analysis. Raven’s gatekeeper evaluates which libraries, functions, and code paths are expected to execute in production and stops builds only when real, exploitable risk is introduced.
How is this different from traditional CI security or SCA tools?
.svg)
Traditional CI security and SCA tools block builds based on CVSS scores, dependency presence, or severity thresholds. Raven blocks builds based on runtime execution likelihood, network reachability, and exploitability, dramatically reducing false positives and unnecessary remediation.
Does Raven replace SCA tools in CI/CD?
.svg)
Raven does not replace SCA inventory or reporting tools. It replaces noisy, severity-only CI gates by adding runtime-aware enforcement.
What causes a build to fail in Raven CI/CD Gatekeeper?
.svg)
A build fails when at least one configured policy control fails. Controls can include:
- Vulnerable functions expected to execute at runtime
- Runtime-loaded vulnerable libraries
- Network-reachable vulnerabilities
- Known exploited or high-probability vulnerabilities
- Malicious packages
- Exposed secrets
- Disallowed open-source licenses
Each control is evaluated independently.
Does Raven block builds for unused or dormant vulnerabilities?
.svg)
No. Raven does not block builds for vulnerabilities that are not expected to execute in production. Dormant libraries, unused code paths, and unreachable vulnerabilities are ignored by default.
How does Raven predict runtime execution during CI?
.svg)
Raven uses historical and live runtime intelligence collected from production environments to model execution behavior. This data is applied during CI/CD to predict which components in a new build are likely to run in production.
Does Raven support secrets scanning in CI?
.svg)
Yes. Raven detects leaked secrets, credentials, and sensitive tokens during the build process and can automatically fail the pipeline when secrets are found.
How are policies configured in Raven CI/CD Gatekeeper?
.svg)
Policies are defined using composable controls with clear thresholds. Teams can combine runtime-aware controls with exploitability, malware, secrets, and license rules. No custom code is required.
Can teams create exceptions without disabling security?
.svg)
Yes. Raven supports granular, scoped exceptions per policy or artifact, allowing teams to unblock specific cases without weakening the overall gate.
Does Raven slow down CI pipelines?
.svg)
No. Policy evaluation is performed during the build process and is designed to be fast and deterministic, with clear pass/fail outcomes.
What happens if a risky build passes CI but is later exploited?
.svg)
Raven enforces the same intelligence at runtime using Raven ADR, providing prevention and detection even after deployment.
Who typically uses Runtime CI/CD Gatekeeper?
.svg)
Raven CI/CD Gatekeeper is used by:
- Application Security teams
- DevSecOps teams
- Platform and infrastructure security teams in cloud-native environments with frequent deployments and large open-source dependency trees.
Is Raven CI/CD Gatekeeper only for Kubernetes and containers?
.svg)
No. Raven CI/CD Gatekeeper works across containerized and non-containerized environments. It enforces security policies during artifact and image build for cloud-native platforms, traditional VM-based deployments, and on-prem or hybrid environments - before code reaches any runtime, including Kubernetes.
Resources
%20DeepDive.png)
Security
A deep analysis of React2Shell (CVE-2025-55182) RCE in RSC Flight protocol—and why WAF rule patches fail to protect modern React and Next.js apps.
Read more
.png)
Security
Learn why true reachability means detecting executed vulnerable code, not just used libraries, and how this shift cuts SCA noise by 97%.
Read more
.png)
Product
Learn how to debug eBPF verifier errors, manage instruction count limits, and optimize your eBPF programs for performance and safety. Discover practical tips on tail calls, maps, helper functions, and measuring instruction counts effectively.
Read more
.svg)

