.avif)
You Can’t Stop Runtime Attacks From the Outside.
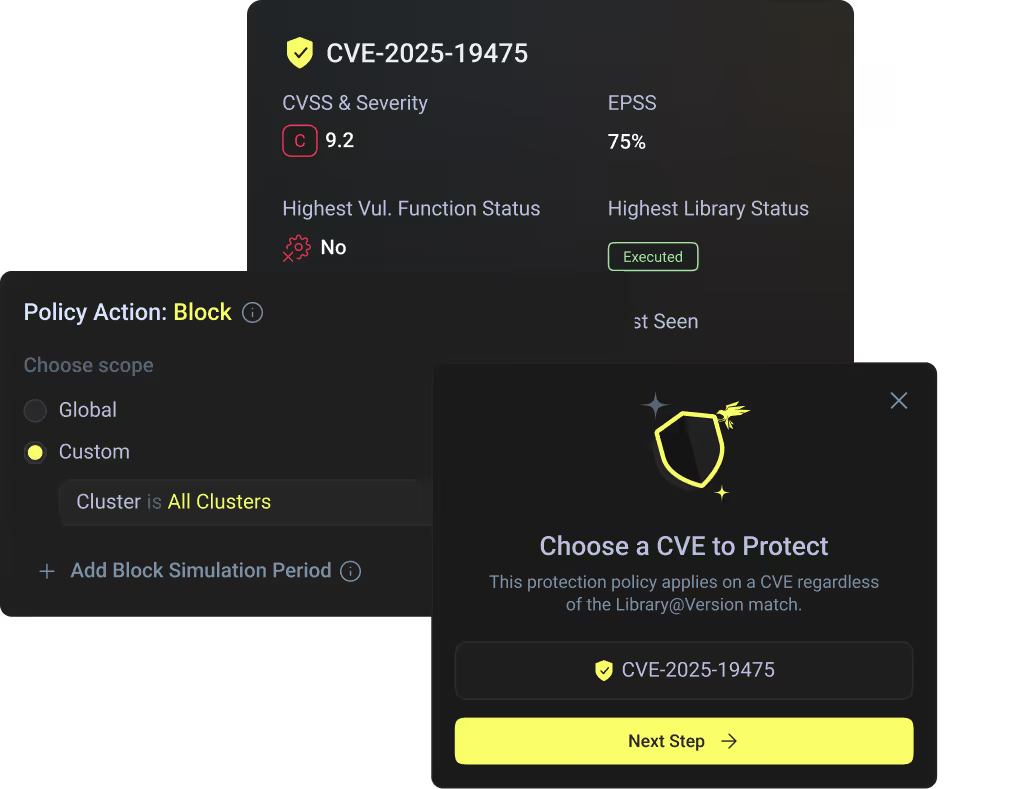
Raven runs inside the application runtime to stop malicious code execution before it ever runs - whether a CVE exists or not.
Stop malicious code execution before it ever runs. CVE or no CVE.
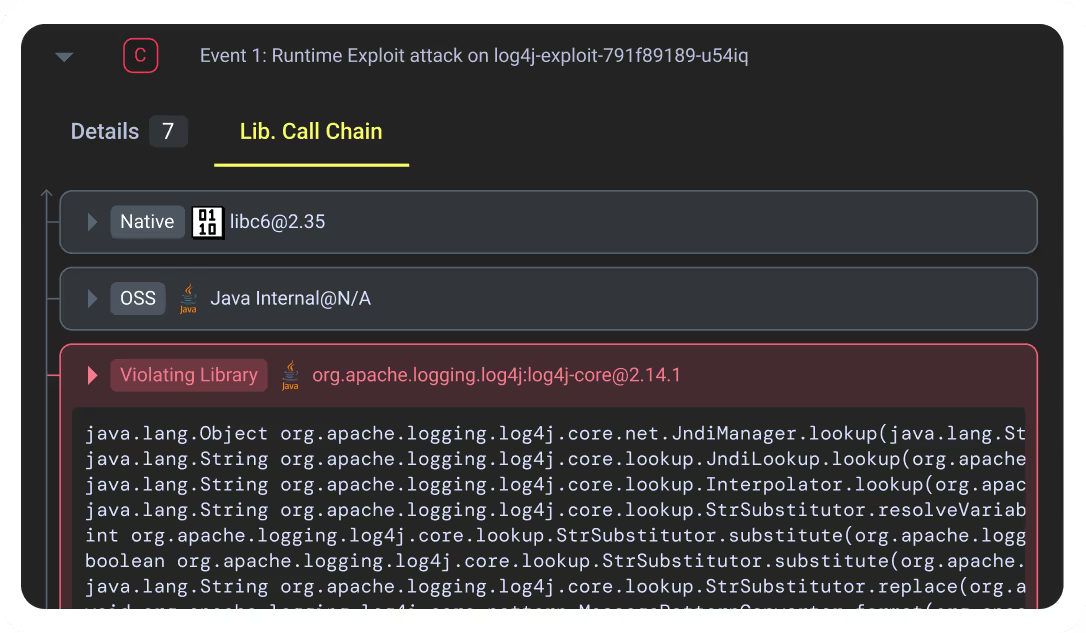
Detect and respond to application attacks with deep application-level forensics.
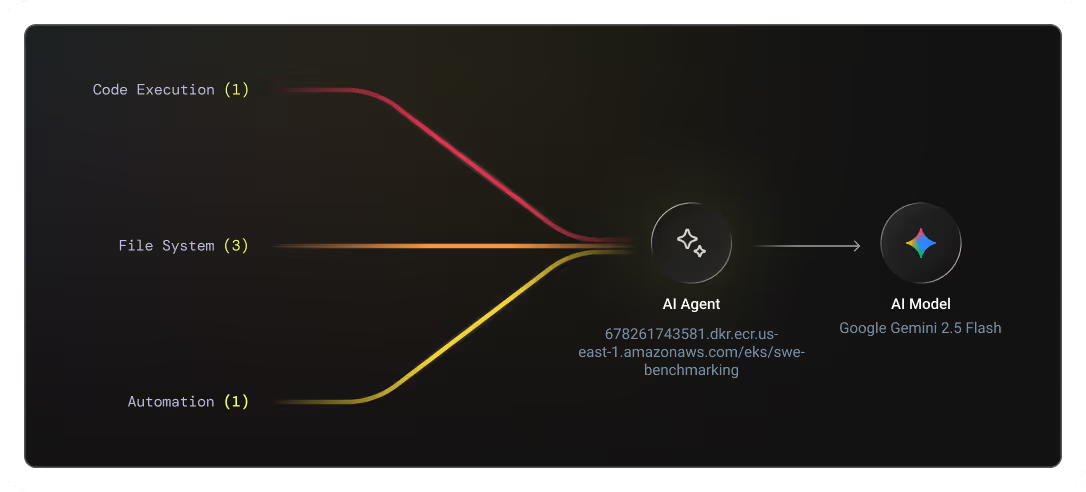
See every agent. Eliminate rogue and shadow AI agents.
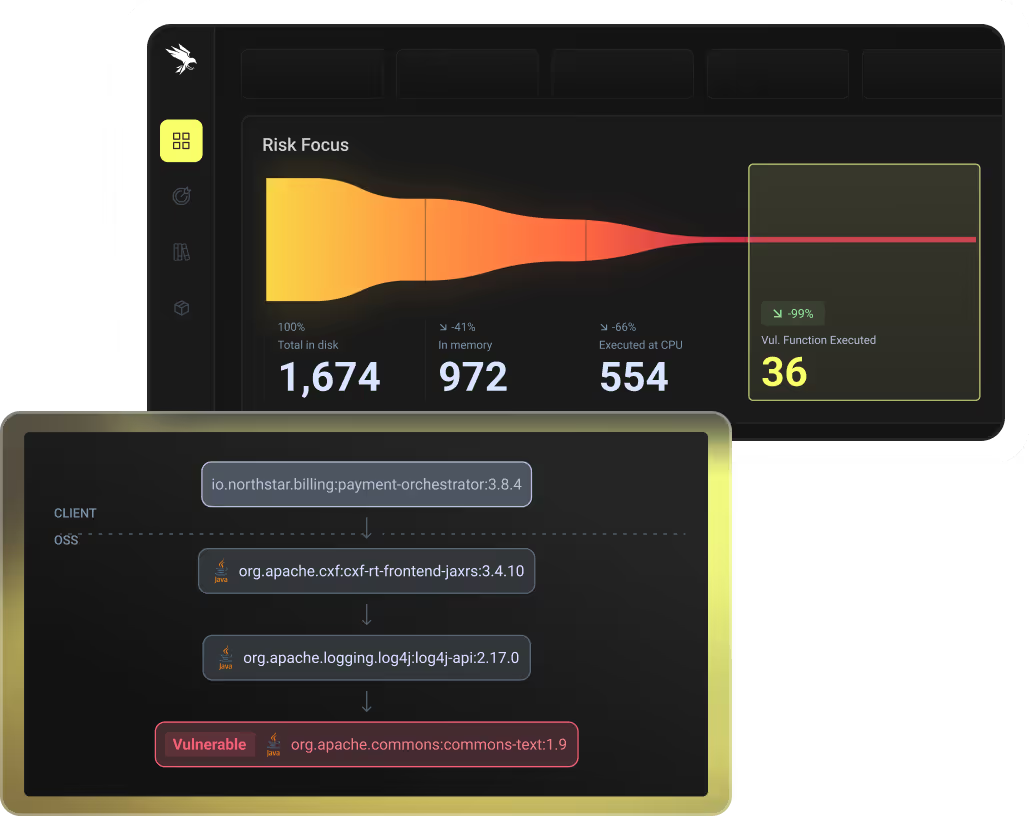
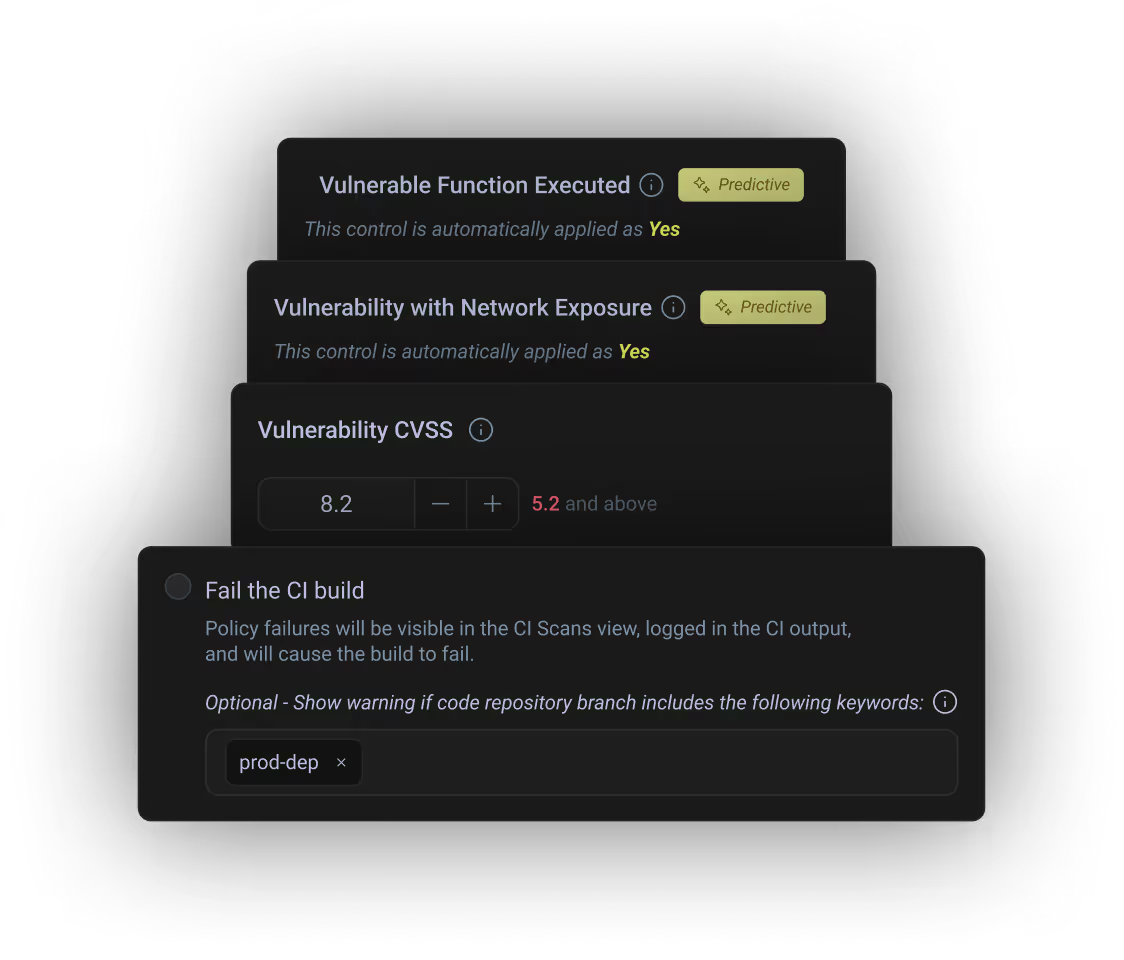
De-prioritize 99% of vulnerabilities - and get actionable remediation plans for the rest.
Predict and block risky applications before they ever reach production.
Runtime SCA


.svg)


.svg)
.svg)
















.png)

.png)
